For companies trying to create employee desktops stored on a server and delivered over the internet, security and optimization often entail a mess of vendors, settings, and updates. Thankfully, two of the biggest names in the industry just announced a partnership that aims to simplify the whole process.
Virtualization giants are pairing up
Online video chat enhances customer service
Microsoft Teams is updated and ready

Prior to the release of Microsoft’s version of Slack -- a popular cloud-based team collaboration tool --, Microsoft Teams received a major update that might have given it the competitive edge. Enhanced communications aren't the only way productivity will be driven; take your business to greater heights with these new features.
Disable Microsoft’s new desktop ads

Digital advertisements are ubiquitous across the internet. And just as users started to come to terms with that, Microsoft has taken ads one step further. The Windows File Explorer has begun to show ads for services like O365 and OneDrive, and if you’re wondering how to disable them, this article is for you.
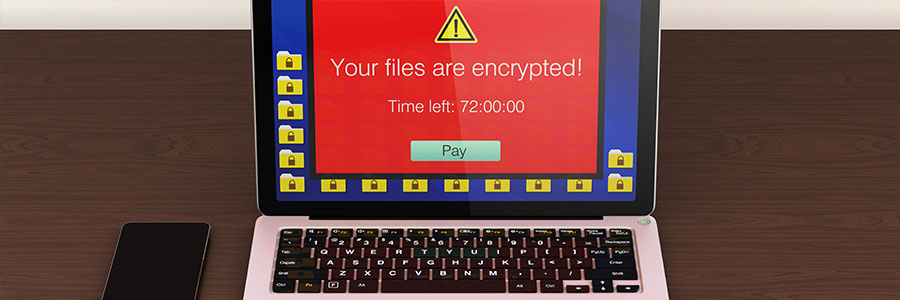
No Ransom: a place for free decryption
Mac ransomware and how to defeat it
Google makes its cloud platform Always Free
OMS: The best way to organize online sales
Cloudbleed: Your data could be at risk
Why your business needs a hardware firewall

Cybersecurity is one of the final bastions of hardware superiority. More and more IT solutions are being hosted in the cloud, and business owners are being told that software is all they need to get the job done, which is half true. When it comes to perimeter security you definitely need a hardware firewall, with a little something extra.